
The purpose of this article is to highlight that the existing security checks protect only recipients of money, not the victims of online banking frauds.
According to John Detrixhe ((https://uk.linkedin.com/in/john-detrixhe-b808856, November 12, 2019), Future of Finance Reporter at Quartz (a digitally news outlet), last year the growth of cashless transactions (CTs) in India (55% ) was far ahead of China (48%) and UK (10%). In India, CTs gathered momentum after demonetisation in in November 2016. The RBI expects growth rate to remain fast. Due to the fear of currency notes spreading corona virus, people are being advised to do, as far as possible, CTs. Several times RBI Governor appeared on TV channels advising people to make online payments for goods or services.
With fast global shift to CTs, the number of service providers has also increased. In India alone, there are more than 45 mobile wallet providers, and some 50 UPI-based wallet providers. Banks have been proving the service through debit and credit cards and facilities for on-line inter-bank as well as inter-bank transfers.
The increase in volume of CTs has opened a new ‘opportunity’ to thieves also. Cybercrime is steadily increasing. On February 4, 2020, Union Minister of State for Home G Kishan Reddy informed the Lok Sabha that nearly 6,900 cases of online banking frauds were registered in the country in 2017-18. He added that with the rapid increase in use of cyber space, the number of cybercrime is also increasing.
According to survey by FIS, a financial services technology provider (2018) India has the highest rate of online banking frauds in the world. In December, Ravi Shankar Prasad, IT minister said that there were over 25,800 cases of digital fraud in India in 2017. According to a news item dated Feb11, 2020 in the Hindustan Times, RBI’s reply to a right-to-information (RTI) query revealed that over a period of 10 years (April 2009 to September 2019), fraudsters siphoned off ₹615.39 crore in more than 1.17 lakh cases of credit and debit card frauds. The number does not include cybercrimes amounting to less than ₹1 lakh between April 2009 and April 2017. According to a news item in Mail Today (April 23, 2020), a New York based cyber intelligence firm IntSights and other cyber security researchers have also warned against spike in cybercrimes during the present period of crisis caused by coronavirus.
From time to time, RBI issues regulations to improve security measures. Banks tell their customers to follow security measures such as not disclosing credit/debit card No., EVV and one-time password (OTP, i.e. 6-digit numeric PIN). On January 15, 2020, RBI issued a fresh notification that new credit or debit cards issued after March 16 will work only for domestic card transactions at ATMs or point of sale terminals. If a consumer wants it to do more, he/she will have to enable such functionality through the banking app, internet banking, or by calling the bank or visiting its branch. (The notification does not cover mobile based wallet providers.)
There are instances of banks not following RBI regulations. Fraudsters succeed in breaching the security walls because, due to ignorance or when unconsciously customers share forbidden information. The news item published in the Hindustan Times mentioned earlier points out that “In a survey conducted by online marketplace OLX in February 2020, in which 7,500 people participated, it was found that 52% of the respondents publicly shared their phone numbers and personal addresses online and 26% of them shared OTP with others. Around 22% admitted to sharing bank account, UPI (Unified Payments Interface), credit or debit card PIN details.”
Another modus operandi of fraudsters is to create their own websites, open bank accounts and offer goods or services at attractive prices. When they realise that it was not safe to continue, they close the shops and vanish.
The use of advanced technologies such as web application attack, ransomware and reconnaissance by fraudsters has made cybersecurity a difficult task.
My personal experience is that while banks do not always follow RBI instructions, security measures have been devised to protect banks and wallet providers from any liability. The message is very loud and clear: ‘Take care of yourself. We have told you how to protect yourself.’
The existing security measures do not take into account the fact that all users are not familiar with the technical details of CTs, tricks used by fraudsters and unconsciously become victims. When such customers complain to their bank or wallet providers, the common reply is, ‘Sorry, payment was made after you followed the prescribed procedure’ whereas the fact is that it was the fraudster who collected all the information from the customer and followed the procedure for transfer of money. When a victim of fraud pursues his complaint, bank or wallet provider advises him to lodge a complaint with cybercrime cell of police.
For a common person, it is very difficult to make police act fast to catch fraudsters and recover money. I have learnt it at my cost.
I realised the weakness of the system first time in July 2016 while making an online payment through ICICI bank credit card for a software. To my utter shock and surprise, amount was paid without OTP. After receiving confirmation of payment, I sent an email to the bank to enquire how the payment was made without OTP. The bank’s reply was even more shocking: ‘The merchant’s bank has not complied with the RBI regulation effective from August 1, 2009. Hence the PIN was not asked and your card transaction went through without the mandatory requirement of entering the 6-digit numeric PIN.’ The bank advised me to “always transact on websites/with merchants that are 3D-Secure authenticated.” ((https://www.devendranarain.dev/2016/08/your-credit-card-may-be-used-without.html)
Since the company to which I had made the payment was genuine, I did not lose money but I wrote to the bank, “A credit card holder may not know that the website/merchant is not 3D-secure authenticated. He relies on you to protect his interest. I request you to please bring such cases of violation of regulation to the notice of the RBI.” The bank sent a standard reply that the feedback would be used to improve the service. Despite reminders, t the bank never told me whether non-compliance of regulation about ‘no payment without six-digit PIN’ was brought to the notice of the RBI or not.
Very recently, on March 12, 2020, for the first time I really became victim of cyber fraud. I have been using debit/credit cards for over two decades and Paytm for about 18 months. I admit, I became a victim entirely due to my fault.
On that unfortunate day, I received SMS from “PAY,,TM” that ‘unless KYC is updated, my “Pay,,tm” account will be blocked.’ I was asked to contact on 8388095829. I have a Paytm account. Without noticing, the difference in the spelling, I proceeded to update KYC (actually, to fall in the trap). When contacted, one Manish Kumar chatted on Quick Support (on mobile), collected photo of driving license for ID proof and details of ICICI credit card for linking it to Paytm.
By the time I realised that I had become a victim of cybercrime, 3 amounts – Rs. 9999/- (PAUPAYMENTS), Rs. 4990/- (Accelyst Soluti.Avbl) and Rs. 9990/- (PAUPAYMENTS) – (total Rs.24,979) had been collected from my ICICI bank Visa credit card No. 4375 51XX XXXX 5015. Since I had not made any payment for anything purchased, it was a clear case of fraud.
Immediately, I blocked the card and emailed complaints to ICICI Bank and Paytm. After collecting details of what had happened, both washed their hands off. The bank told me that since the payments had been made after due authentication, ‘the bank will not be able to raise any further claims on your behalf with the merchant and refund the amount involved in the transaction.’ Paytm replied that since the transaction did not belong to Paytm, it would not do anything. They did not bother that it was a case of online fraud.
On the same day (March 12), I lodged an online complaint with the Cyber Crime Cell of Gurugram Police on its website. I did not get any acknowledgement or response. On March 19, I tweeted my complaint drawing the attention of Haryana Chief Minister. Thereafter his office collected my phone number. Two days later, on March 21, a policeman of cybercrime cell contacted me to get the details. The complaint No. is 1473-5p 2 dated 20-03-2020. (The cell could not trace my complaint of March 12). As required by the cell, I emailed complete account of what had happened on and after March 12.
In my email, I pointed out that
- Even if I lost money due to my fault, theft is theft and a criminal who has stolen the money remains a criminal. The criminal cannot be pardoned because he took advantage of my mistakes.
- Even if the ICICI bank is helpless (which is not true), the criminal can be traced with the help of the payment gateways through which the amounts were transferred to his bank account and the bank to which the amounts were transferred’
- The payment gateways can tell the police name of the bank, address of the branch and account number.
- The bank to which the amounts were transferred can easily identify the fraud. No bank is supposed to accept the request of opening a bank account without proper verification of name and address, Adhaar No. and PAN. KYC is mandatory.
Had the cyber cell of Gurugram police acted promptly, the fraudster could have been caught immediately. His mobile No. 8388095829 was active at least till forenoon of March 16, 2020. When I got that mobile No. checked by TRUE CALLER, reply was that it was used for KYC FRAUD.
On April 1, 2020 I received a phone call from the same policeman of the Cybercrime Cell. He wanted to know the date of crime! Obviously, even nine days after the registration of complaint, he had not bothered to read it. The same day, I sent identical emails to (1) Anil Viz, Home Minister, Haryana, (2) Manoj Yadava, Director General of Police and (3) Muhammad Akil, Police Commissioner, Gurugram. In emails, I gave full account of what had happened on March 12 and developments thereafter and requested each one of them to direct the Cyber Crime Cell, Gurugram Police, to expeditiously complete investigation and catch the criminal. Needless to say, there was no response. No action has been taken till date (April 25, 2020).
On April 22, to draw the attention of PAYU PAYMENT (@PayUIndia) and Accelyst Solution gateways, used by the fraud, I tweeted that these gateways are very helpful to cybercriminals. After 24 hours, @PayUIndia sent a message asking me to share details which I did but it refused to disclose the name of the recipient. It advised me “to follow up with cybercrime cell, they will contact us and all necessary details will be provided to them”
In nutshell, credit card issuer, wallet service providers and gateways share “secret” information only with cybercrime cell but the latter does not bother when victim is a common man. Home Minister and senior police officers are also not bothered when common persons become victims of online banking frauds.
After bitter experience, I decided to analyse various modes of transfer of money and to find how CTs can be made safer i.e. how to protect customers even if they commit the mistake of sharing secret information with a fraudster.
There are several modes of online transfers of money:
- From one person’s bank account to another person’s bank account (inter-bank and intra-bank).
- From bank account to smart phone operated wallet such as Paytm.
- From customer’s bank account to the bank account of merchant (seller of goods or services).
- From one person’s wallet to another person’s wallet.
- From wallet to bank account.
- From wallet to merchant’s bank account.
- From credit/debit card to wallet.
- From credit/debit card to merchant’s bank account.
My experience is that online transfer of money from one bank to another bank account is the safest. It is done after getting confirmation of all details from the transferor as follows:
| Name of beneficiary XXXX XXXXXX
Beneficiary IFSC Code XXXXXXXXXX Beneficiary Account Number/ XXXXXXXXXXXX Credit Card Number Bank Name xxxx.00 Transfer Type Transfer Now Mode of Communication SMS Communication detail XXXXXXXXX For authorisation of transfer of money, bank sends six-digit ODP that has to be entered. |
For authorisation of payment, bank sends six-digit OTP that has to be entered. There is no chance of fraud even if a fraudster has access to user ID and password to open the net banking window and the transfer pin or the OTP because fraudster will have to add new payee which is not easy because the account holder will get SMS with OTP for confirmation of addition does not come immediately.
Online transfer of money to a merchant’s bank account
The entire process is explained in Appendix. It takes only a few seconds. Payment to merchant’s bank account may be made same day or after a couple of days. (I have not checked time taken by different gateways.)
Who is responsible for online banking frauds?
Whatever the cause of fraud, whatever the modus operandi of fraudster, which of the parties in the loop is or are the main culprit(s)? They are undoubtedly payment gateway and merchant’s bank.
Every fraudster has to open a bank account or should have a wallet account. For opening a bank account he has to furnish several documents such as proof of identity, proof of address, PAN card and two recent passport size photographs. For receiving online payments, merchant and his bank enter into an agreement.
If after all these precautions, the million-dollar question is: how does a fraudster open and operate his bank account?
For mobile-based wallet, the company providing the service verifies all the details furnished by the customer, followed by physical verification at the residence of the customer. When I wanted to have a Paytm account, an executive of the company visited by residents for verification
Again, the million-dollar question is: after all the verifications, how can a fraudster use his wallet for online banking frauds? While it is for the RBI to enquire how fraudsters are able to open bank accounts or wallets, I hold the gateways also as the main culprit. Normally an email confirming payment through credit contains the name of the recipient merchant. However, when the fraud collected amounts in three “transactions”, instead of the name of the “merchant” , each confirmation email mentioned the name of the gateway. Look at the intimation of five transactions, including three fraudulent, to me.
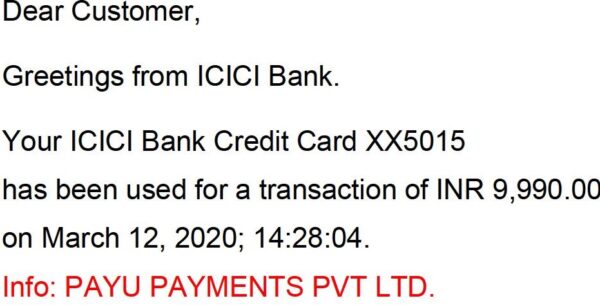
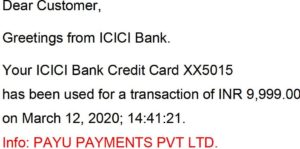
(PAYU PAYMENT is a gateway. The name of the merchant receiving payment is not mentioned. The amounts were collected by online banking frauds)

(Accelyst Solution provides mobile payment services. The name of the merchant receiving payment is not mentioned. The amount was collected by an online banking fraud)
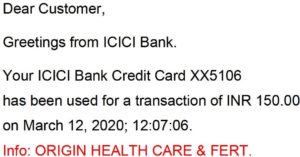
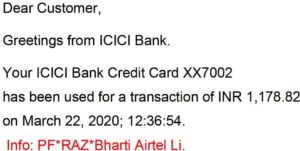
(The above two payments were genuine. In each case the name of the merchant is clearly mentioned)
Cybercriminal would not have succeeded had mentioning the name been mandatory. After analysing the existing procedures, existing security check and my personal experience, I have two suggestions to stop online banking frauds.
- GiftTool or processor or payment gateway should have a software to communicate to the customer – not immediately but after 24 hours – through SMS and email the name of the merchant, name of his bank, his bank account number with IFSC, the amount to be transferred to that account, the way bank informs his customer in case of inter-bank or intra-bank transfer, as shown in the table above. The gap of 24 hours is necessary because at the time transaction is being processed, fraudster may have access to all the communication to the customer. Pending confirmation, the amount to be deposited in merchant’s account should be kept on hold. The amount should be deposited into merchant’s bank account only after customer’s confirmation. If the customer has not taken any action to pay, he will not confirm payment and will be saved from losing his money.
- The above security check may not stop online banking frauds when a customer has placed order with a fraud merchant and is not aware that the merchant is a fraud. To take care of such frauds, the agreement between merchant and his bank (that allows merchant to accept online payments) should not be finalised unless the merchant makes a security deposit of, say, Rs. 5 (five) lakh. If the merchant is not in a position to deposit the amount in one instalment, his receipts should be automatically transferred to the security deposit until the prescribed limit is reached. The security deposit can be used to compensate victims of online banking frauds.
With these two new security checks, it would be impossible for fraudsters to stay in “business”.
In the case of online banking frauds, it is bank’s responsibility to refund money to the customer when he lodges a complaint. A bank cannot have a fraudster’s account and disown responsibility. Similarly, it is wallet service provider’s duty to refund money to the customer when he lodges complaint. A wallet service provider cannot have a fraudster’s account and disown responsibility. A gateway must disclose the name of the recipient.
A telephone call or a voicemail for confirmation will not serve the purpose because it will not produce all the details in black-and-white. (For checking fraud in withdrawal from ATM, if it is decided to provide OTP, it should always be sent as SMS, rather than as voicemail. Many cardholders may not follow the accent of voicemail.
It is easy to stop online banking frauds or at least to reduce it significantly provided RBI understands that and acts.
If readers agree with my analysis and suggested additional security measures to stop online banking frauds, they should please share this article with their friends.
Comments and suggestions are most welcome.
Devendra Narain
Appendix
| Using a computer or smartphone, customer submits to the merchant’s (seller’s) website amount to be paid, information about his bank account for net banking payment or credit card information (card No. Name of the cardholder, three-digit CVV i.e. Card Verification Value) |
| A software, GiftTool, checks entries. If card No. is wrong, error message is flashed for correction. Thereafter, customer receives OTP (through SMS) to be entered. If there are still mistakes in card details, issuing bank refuses to accept. When all entries are correct and OTP has been entered, GiftTool submits information to the merchant’s payment gateway server. |
| Merchant’s payment gateway server (software that provides a link between customer and merchant) sends information to Internet Merchant Account, a bank account for an online business, that allows the merchant to deposit and refund online payments. Merchant and his bank (called the acquirer) enter into an agreement that allows the merchant to process and accept debit/credit card payments. Merchant agrees to abide by the operating regulations established by Card Issuer (VISA, Master Card, etc.). |
| Internet Merchant Account submits transaction details to Credit Card Interchange (a network of financial entities that communicate to manage the processing, clearing, and settlement of credit card transactions) for approval of payment. |
| Credit Card Interchange submits transaction details to customer’s Card Issuer for approval of payment. |
| Using a computer or smartphone, customer submits to the merchant’s (seller’s) website amount to be paid, information about his bank account for net banking payment or credit card information (card No. Name of the cardholder, three-digit CVV i.e. Card Verification Value) |
| A software, GiftTool, checks entries. If card No. is wrong, error message is flashed for correction. Thereafter, customer receives OTP (through SMS) to be entered. If there are still mistakes in card details, issuing bank refuses to accept. When all entries are correct and OTP has been entered, GiftTool submits information to the merchant’s payment gateway server. |
| Merchant’s payment gateway server (software that provides a link between customer and merchant) sends information to Internet Merchant Account, a bank account for an online business, that allows the merchant to deposit and refund online payments. Merchant and his bank (called the acquirer) enter into an agreement that allows the merchant to process and accept debit/credit card payments. Merchant agrees to abide by the operating regulations established by Card Issuer (VISA, Master Card, etc.). |
| Internet Merchant Account submits transaction details to Credit Card Interchange (a network of financial entities that communicate to manage the processing, clearing, and settlement of credit card transactions) for approval of payment. |
| Credit Card Interchange submits transaction details to customer’s Card Issuer for approval of payment. |
| Card Issuer approves or declines the transaction based on customer’s available funds and communicates its decision to Credit Card Interchange. |
| Credit Card Interchange communicates Card Issuer’s decision to merchant’s Internet Merchant Account. |
| Internet Merchant Account relays transaction results to merchant’s Payment Gateway. |
| Payment Gateway relays transaction results to GiftTool. Customer receives an on-screen confirmation message as well as an email confirmation via GiftTool secure servers. |
| Internet Merchant Account deposits appropriate fund for the transaction into merchant’s bank account |
Once order has reached payment gateway, payment processor software becomes operational. It processes requests from the gateway until money reaches merchant account and customer gets confirmation of payment. Victim of online banking frauds realises only when the damage has been done.
(Updated on April 25, 2020)










Leave a Reply